The problem
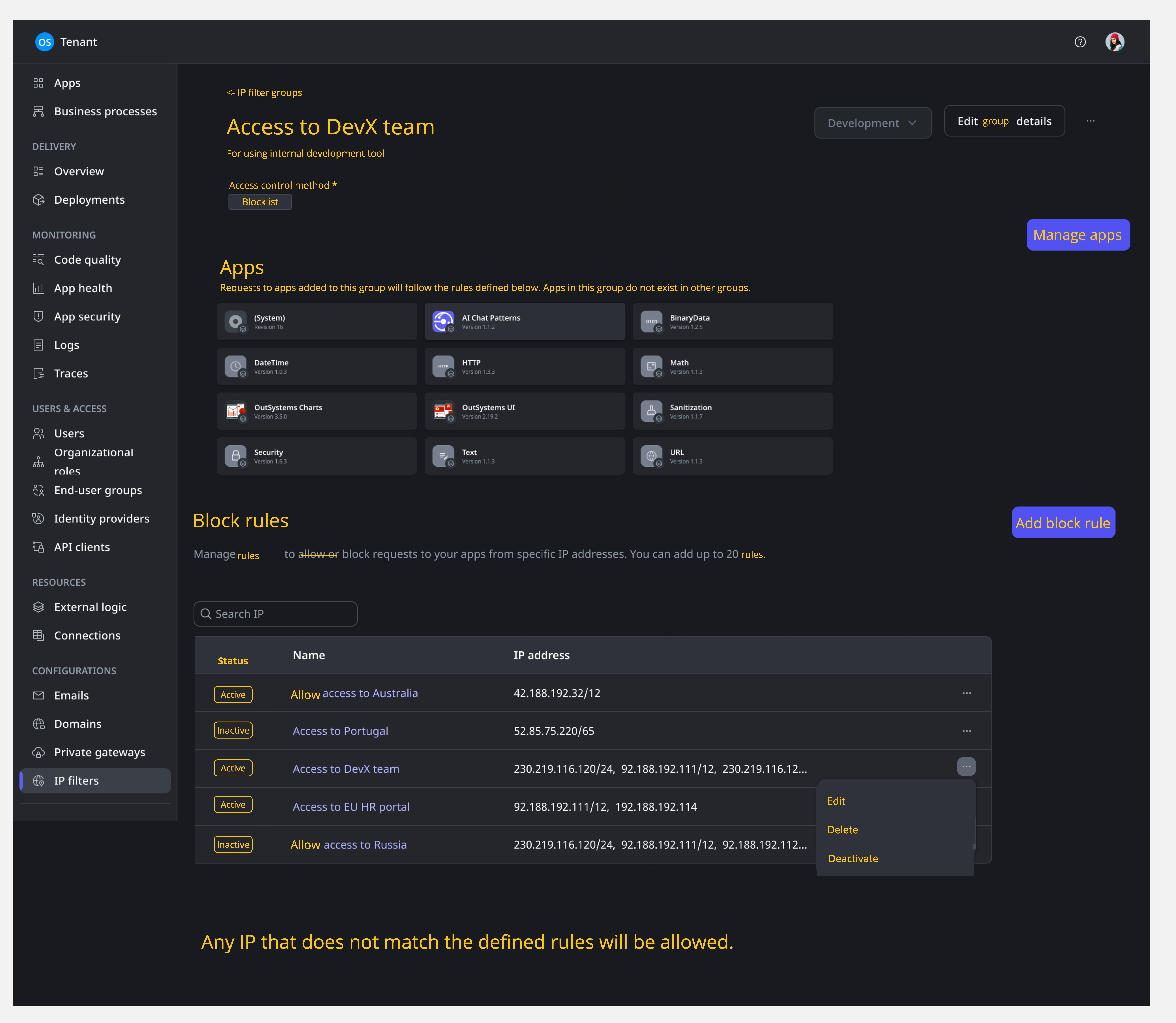
The previous IP filter solution lacked granular control, applying a single set of rules to all applications within a stage. This limitation prevented customers from tailoring security policies to different application groups and posed a challenge for scenarios requiring both restricted and public-facing applications within the same stage. For example, if a customer had a configuration allowing traffic only from certain IP addresses, they couldn't have a public-facing application without disabling IP filters.
Key challenges
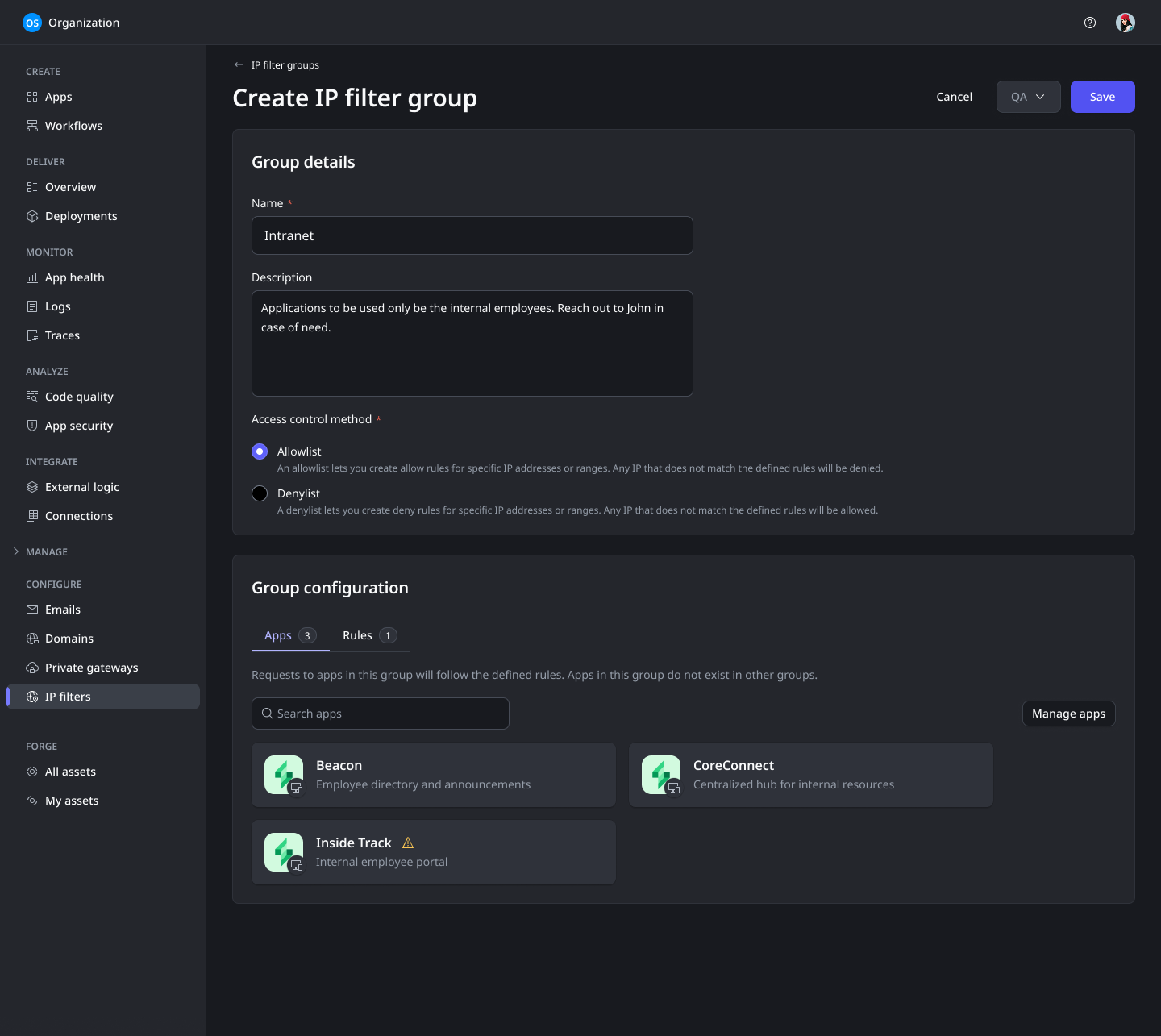
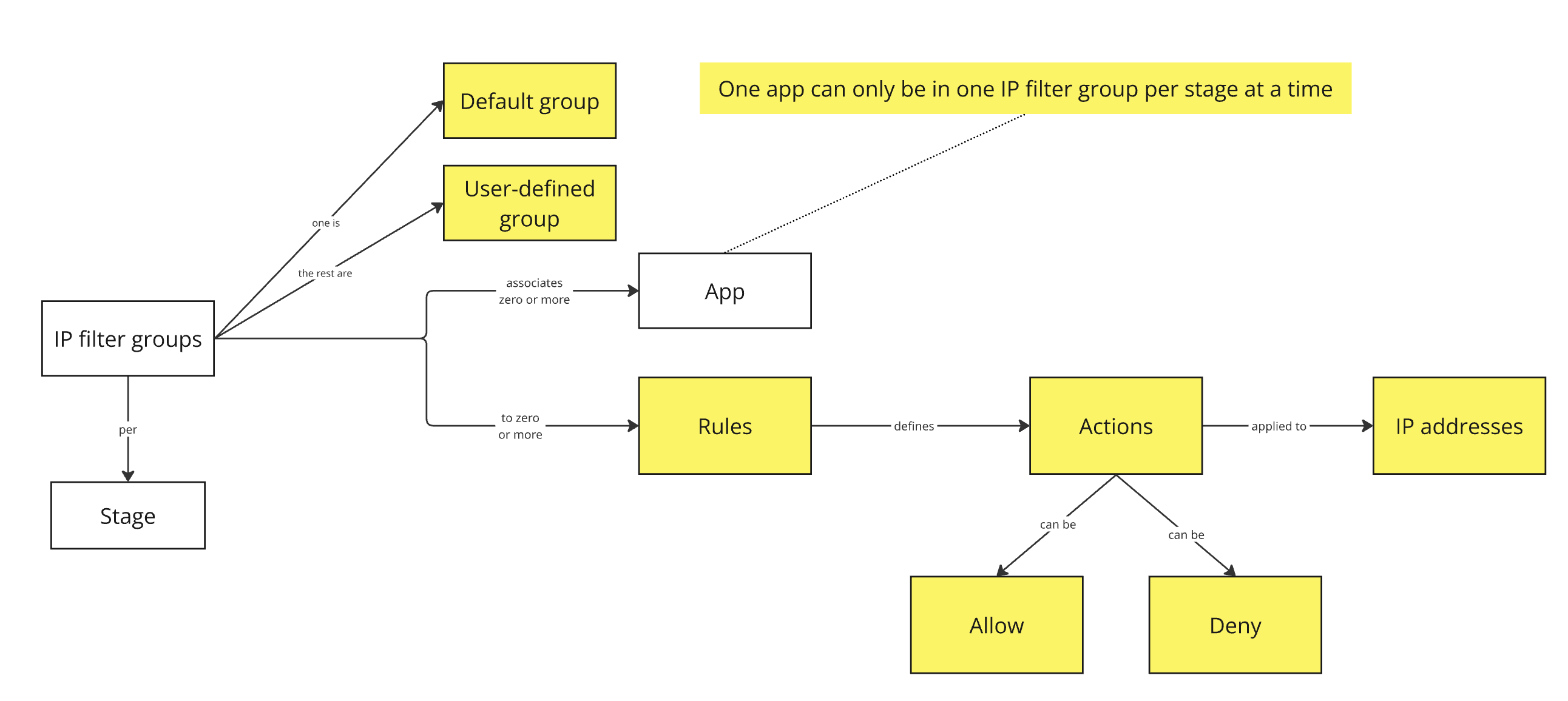
This initiative aimed to allow users to manage their IP rules at the application level, a significant shift from the previous stage-level management. Key challenges included:
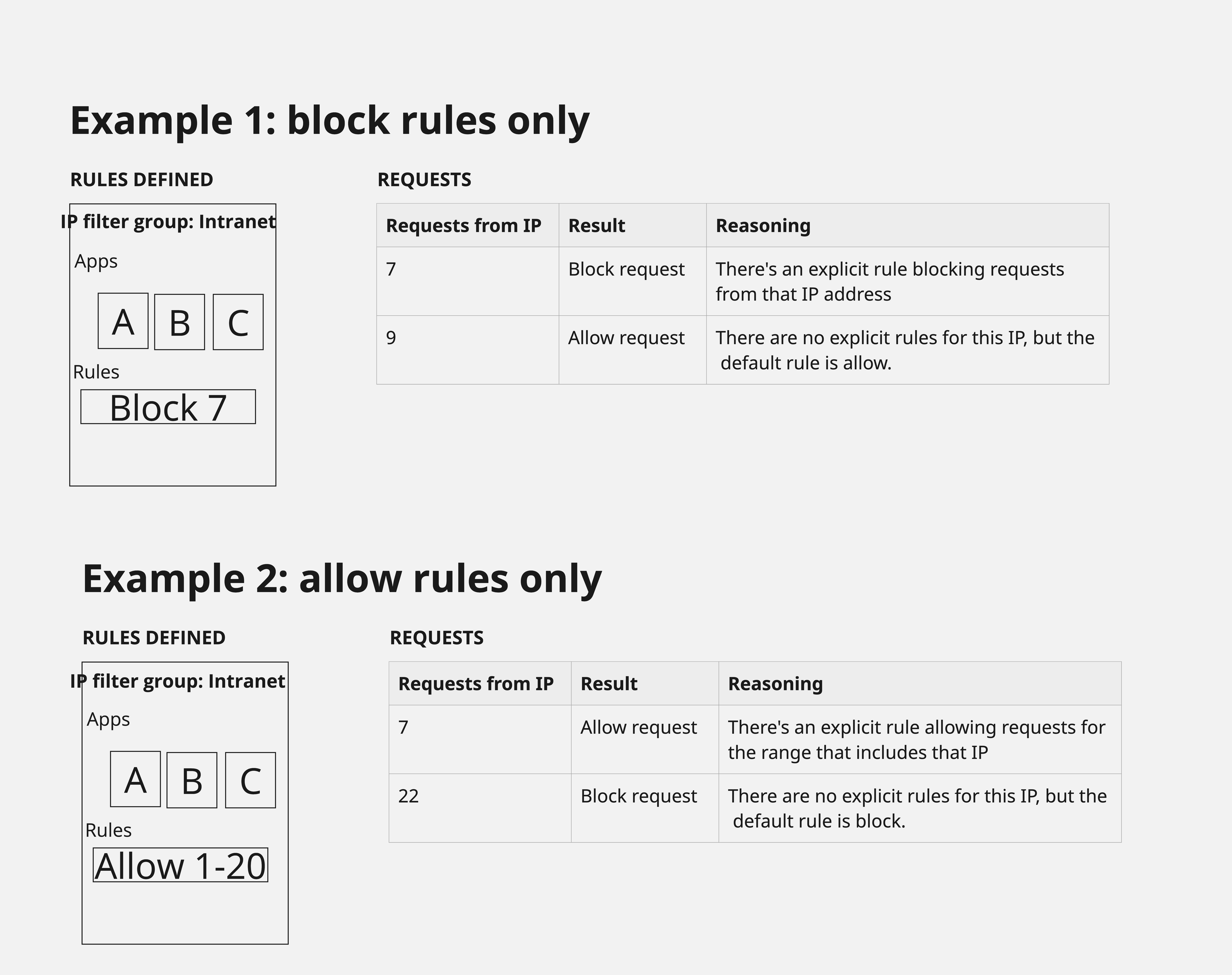
- Technical constraints: there were restrictions in the underlying technology that impacted how IP rules are applied (block rules are applied before allow rules).
- Stakeholder alignment: ensuring high alignment with diverse stakeholders (PM, Engineering, Arch, POs) from the outset was crucial for this architect-intensive problem.